[Introduction:]
Coming soon to Microsoft Teams: A new security feature to enhance external collaboration. If your organization allows external domains to contact users in Teams, we will identify if an external user is impersonating a domain owned by your tenant during their initial contact through Teams chat. If we detect potential impersonation, we will show a high-risk alert to the user, notifying them to check for suspicious name/email and proceed with caution.
This message is associated with Microsoft 365 Roadmap ID 526780.
[When this will happen:]
General Availability: Begins in early December 2025 and expected to complete by mid-December 2025.
[How this affects your organization:]
Who is affected: Organizations that have enabled Teams external access.
What will happen:
- Before rollout: Teams only scanned for brand impersonation risks.
- After rollout: Teams will check for both brand and tenant-owned domain impersonation attempts.
- When impersonation is detected, users will see the warning: “This looks like a spam or phishing attempt” and must preview and validate the sender before accepting the chat invitation.
- The feature will be ON by default for all tenants that allow external access in Teams.
- There are no admin controls to manage this functionality; admins cannot disable this feature.
- No admin configuration changes are required.
- Platform availability: Android, Desktop, iOS, Mac, Web
Screenshot 1 - User sees this warning when the sender is detected as a potential impersonator of the tenant’s own domain. In this example, the sender’s domain is “fabrikarn.com”, which looks like the recipient tenant’s own domain “fabrikam.com”:
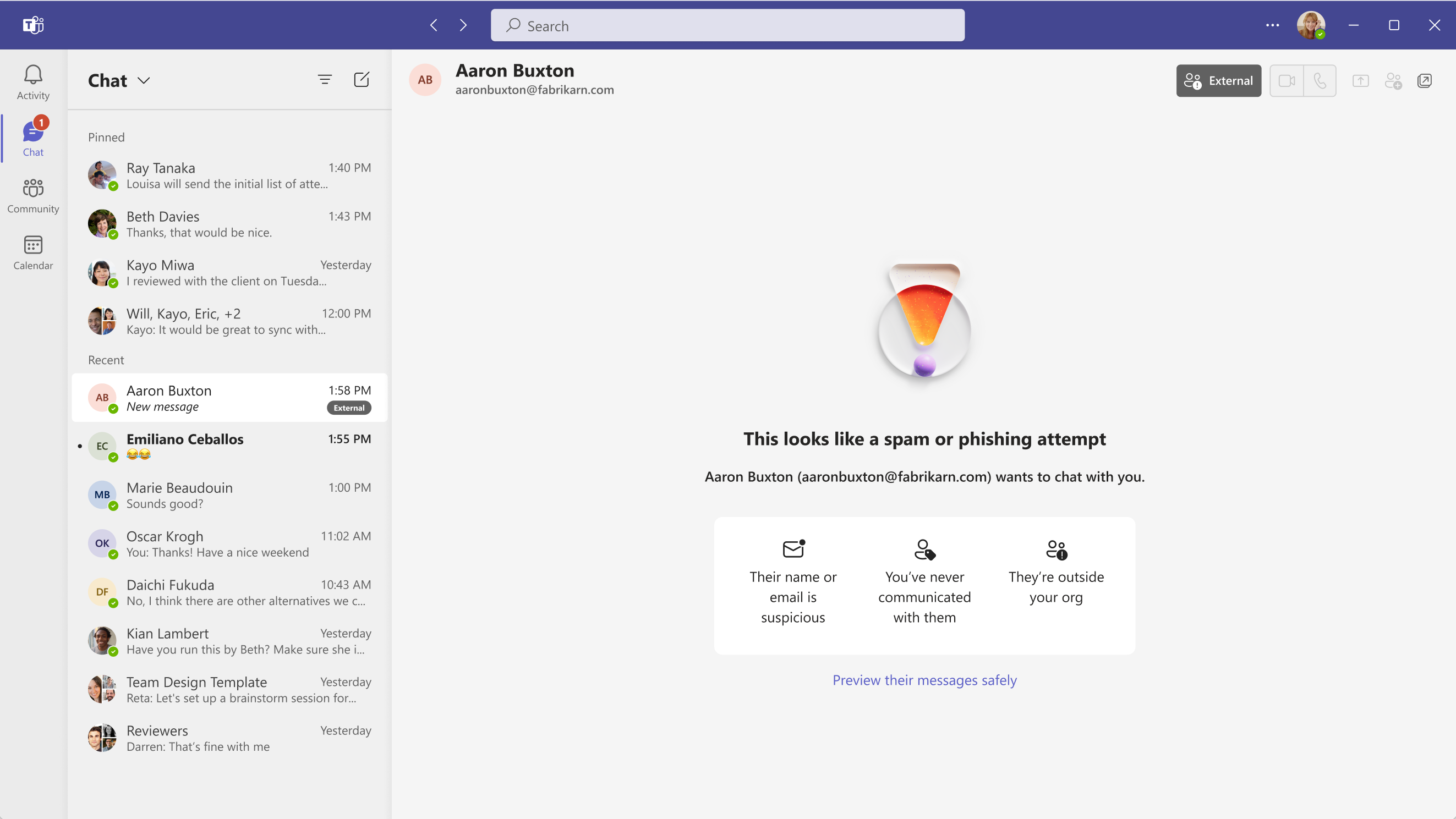
Screenshot 2 - When user clicks on “Preview their messages safely”, they can see the message from the sender, and make the decision of “Accept” or “Block”:

Screenshot 3 - If the user decides to accept, they will be prompted again to check the sender’s legitimacy and confirm that they are not phishing, before the chat is officially accepted:
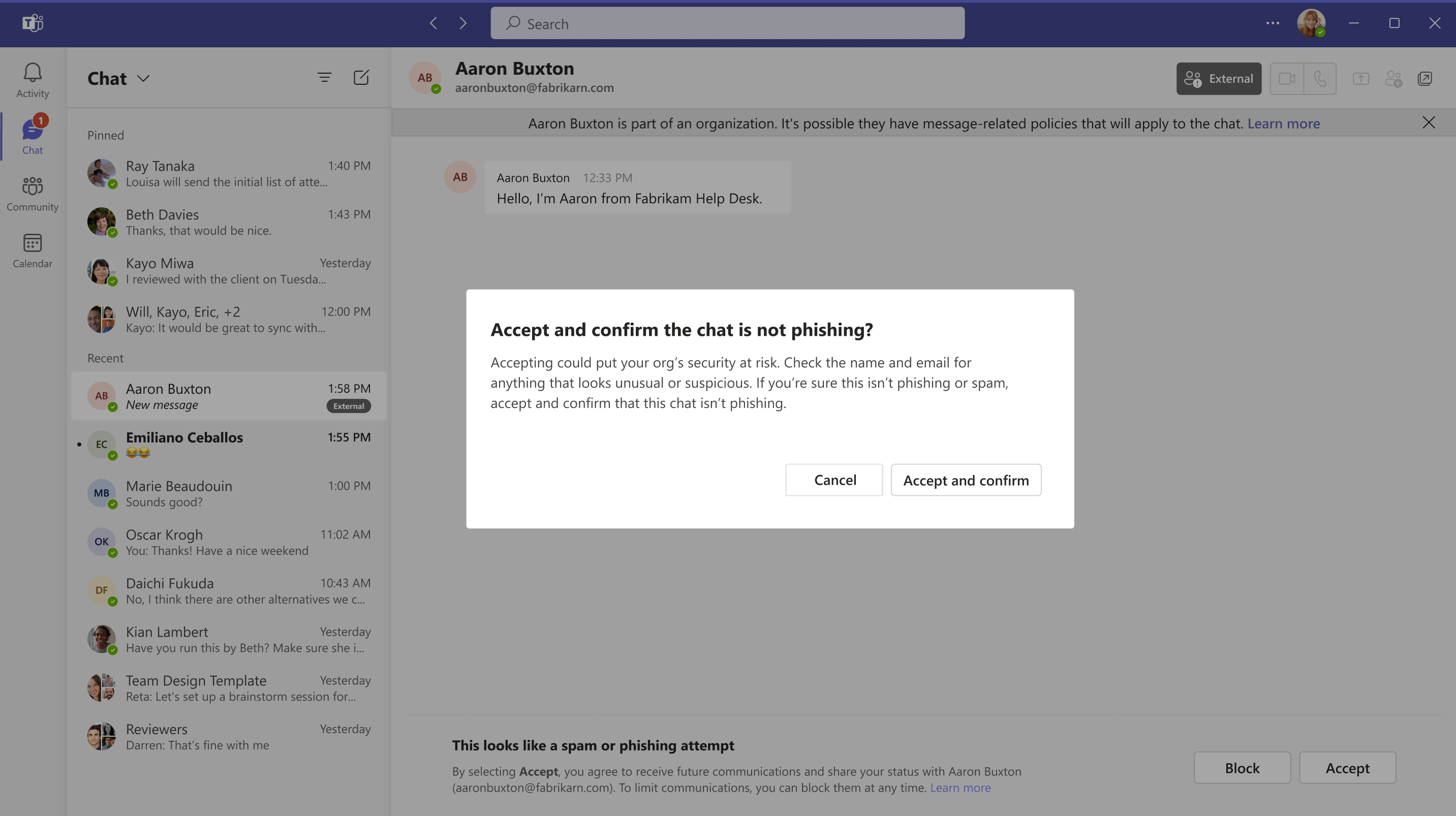
[What you can do to prepare:]
- No action is required; this security check is automatic.
- Admins can review audit logs for impersonation attempts detected.
Learn more: Security and compliance in Microsoft Teams | Microsoft Teams | Microsoft Learn
[Compliance considerations:]
No compliance considerations identified, review as appropriate for your organization.

